Discussion 02 Guide
Question 2
Short Answer!
-
Assume ASLR is enabled. What vulnerability would arise if the instruction
jmp *espexists in memory?ASLR means we have to guess the stack address if we want to execute injected code. However, if there is a
jump *espinstruction in a piece of memory that is not ASLR’d (e.g., text in most ASLR implementations), we can use this to find our way into the stack.The attacker could first do the following:
- Find the address
Xto thejump *espinstruction. - Overwrite the return address to be
X.
Remember the memory layout of a program in the middle of executing a function:
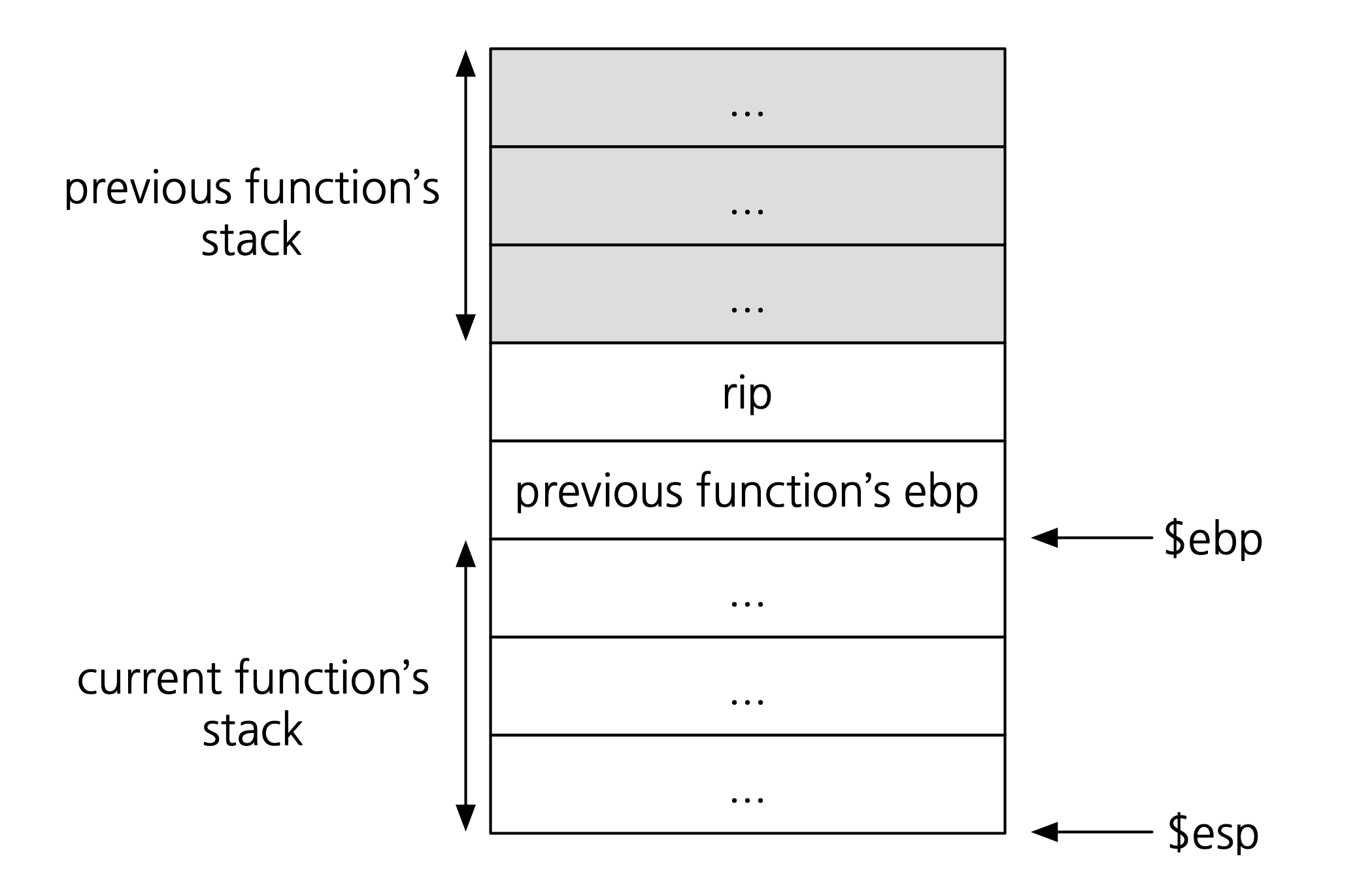
Now, recall the function exit:
mov $ebp $esp pop $ebp ret // pops into $eipAfter
ret, this is what our program’s memory looks like: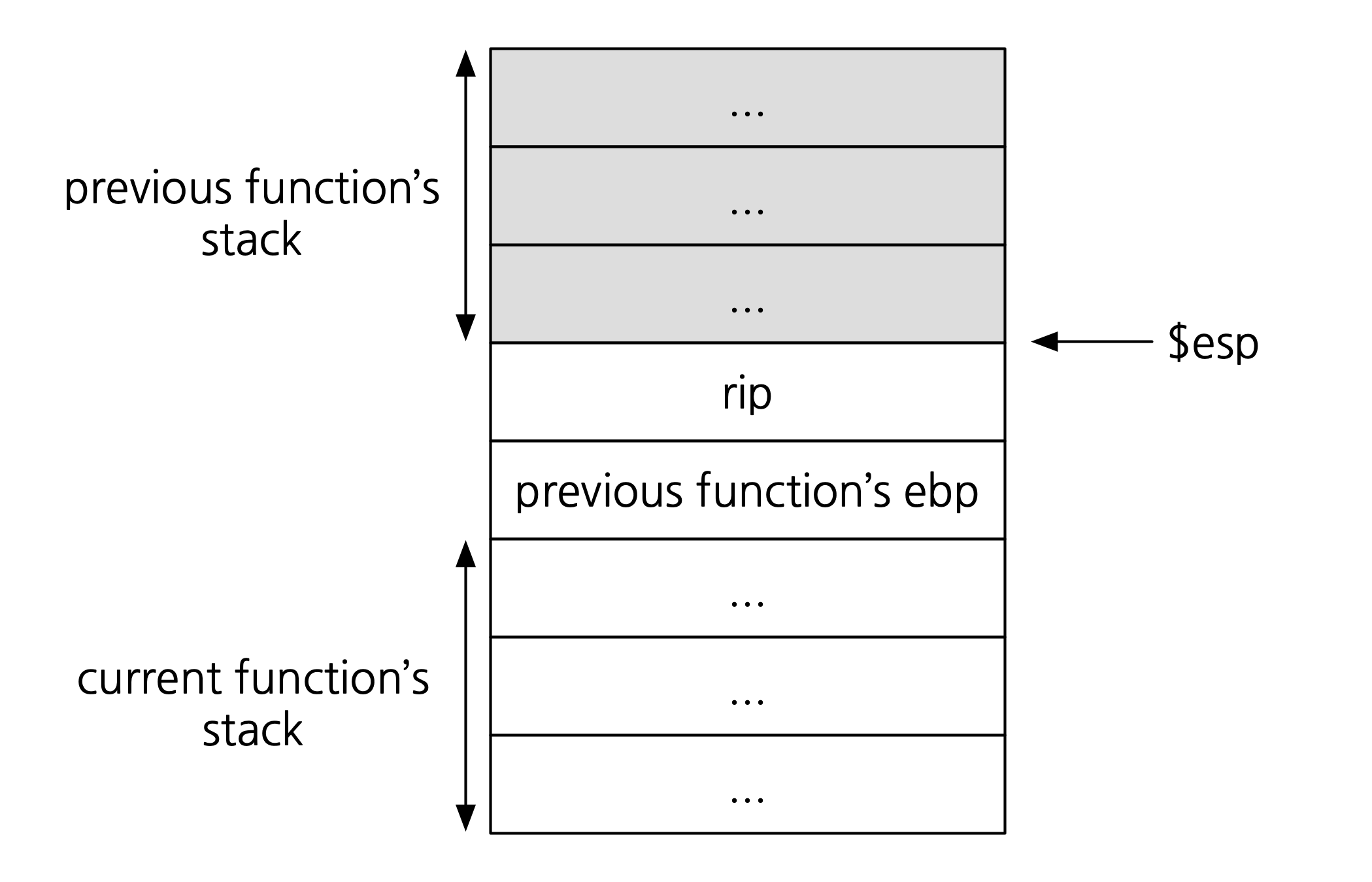
If the attacker accomplished steps 1 and 2, our program would then execute the instruction
jump *esp. This means the first word at the bottom of the previous function’s stack would be executed as an instruction: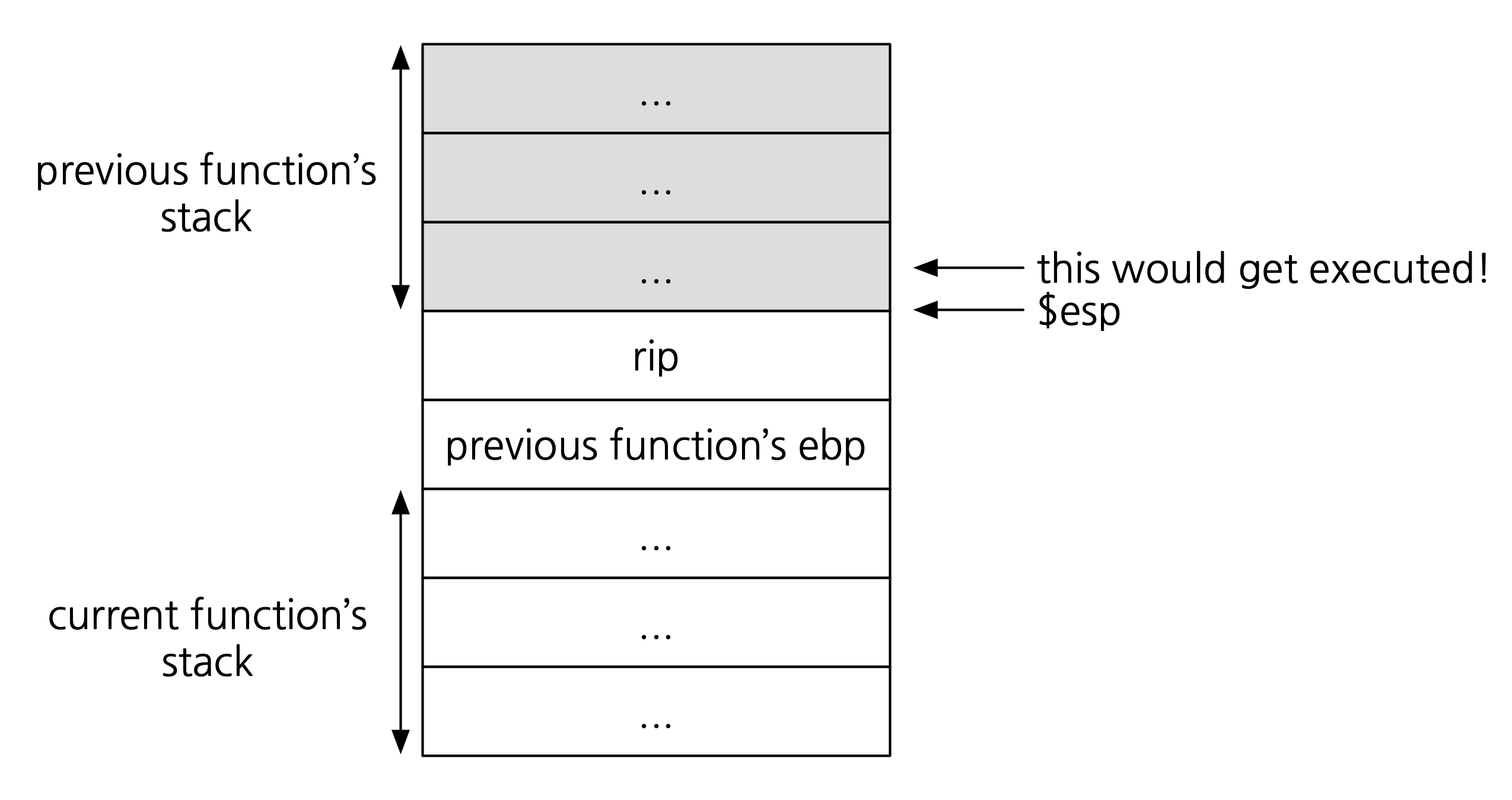
How can the attacker exploit this? One way would be to have that one instruction jump to another location. The attacker could insert shellcode at that new location, e.g., after the
rip: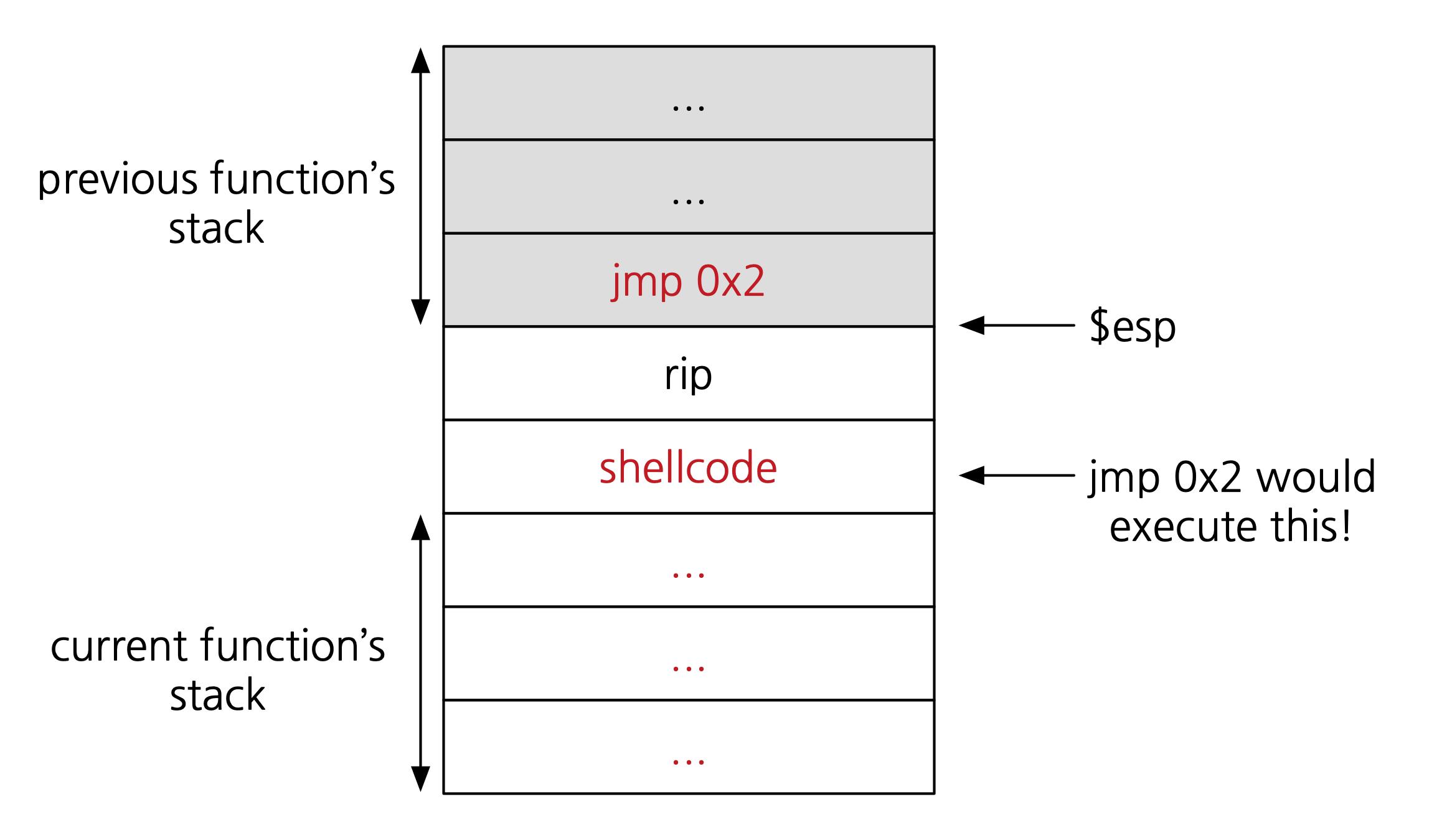
In summary, the attacker could do the following to execute shellcode:
- Write shellcode after the current function’s
rip. - Write
jmp 0x2in the word before therip. - Find the address
Xto thejump *espinstruction. - Overwrite the return address to be
X.
- Find the address
Question 3
Fun reading: Reflections on Trust by Ken Thompson.